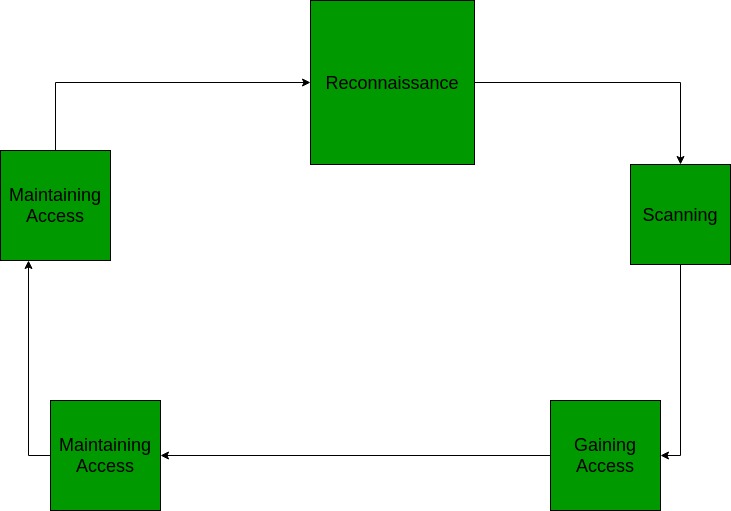
5 Phases of Hacking process
1-Reconnaissance
2-Scanning
3-Gaining Access
4-Maintaining Access
5-Covering Tracks
read also = process of hacking
read also = The Five phases of hacking process
read also = 5 step hacking process
read also = 5 step hacking process
The Five phases of hacking process
1-Reconnaissance
:- This is the essential stage where the Hacker tries to gather however much data as could be expected about the objective. It incorporates Identifying the Target, discovering the objective's IP Address Range, Network, DNS records, and so on.
2-Scanning:- It includes taking the data found amid surveillance and utilizing it to look at the system. Apparatuses that a programmer may utilize amid the filtering stage can incorporate dialers, port scanners, organize mappers, sweepers, and helplessness scanners. Programmers are looking for any data that can enable them to execute assault, for example, PC names, IP locations, and client accounts.
2-Scanning:- It includes taking the data found amid surveillance and utilizing it to look at the system. Apparatuses that a programmer may utilize amid the filtering stage can incorporate dialers, port scanners, organize mappers, sweepers, and helplessness scanners. Programmers are looking for any data that can enable them to execute assault, for example, PC names, IP locations, and client accounts.
read also = process of hacking
3 Gainig access :- In this stage, programmer outlines the diagram of the system of the objective with the assistance of information gathered amid Phase 1 and Phase 2. The programmer has got done with counting and examining the system and now conclude that they have an a few alternatives to access the system.
For instance, say programmer picks Phishing Attack: The programmer chooses to take no chances and utilize a straightforward phishing assault to get entrance. The programmer chooses to penetrate from the IT division. They see that there have been some ongoing contracts and they are likely not up to speed on the methodology yet. A phishing email will be sent utilizing the CTO's genuine email address utilizing a program and conveyed to the specialists. The email contains a phishing site that will gather their login and passwords. Utilizing any number of alternatives (telephone application, site email caricaturing, Zmail, and so on) the programmer sends an email asking the clients to login to another Google gateway with their accreditations. They as of now have the Social Engineering Toolkit running and have sent an email with the server deliver to the clients concealing it with a bitly or tinyurl.
For instance, say programmer picks Phishing Attack: The programmer chooses to take no chances and utilize a straightforward phishing assault to get entrance. The programmer chooses to penetrate from the IT division. They see that there have been some ongoing contracts and they are likely not up to speed on the methodology yet. A phishing email will be sent utilizing the CTO's genuine email address utilizing a program and conveyed to the specialists. The email contains a phishing site that will gather their login and passwords. Utilizing any number of alternatives (telephone application, site email caricaturing, Zmail, and so on) the programmer sends an email asking the clients to login to another Google gateway with their accreditations. They as of now have the Social Engineering Toolkit running and have sent an email with the server deliver to the clients concealing it with a bitly or tinyurl.
read also = process of hacking
read also = The Five phases of hacking process
read also = 5 step hacking process
read also = The Five phases of hacking process
read also = 5 step hacking process
read also = 5 step hacking process
- Maintaining Access: Once a hacker has gained
access, they want to keep that access for future exploitation and
attacks. Once the hacker owns the system, they can use it as a base to
launch additional attacks.
In this case, the owned system is sometimes referred to as a zombie system.Now that the hacker has multiple e-mail accounts, the hacker begins to test the accounts on the domain. The hacker from this point creates a new administrator account for themselves based on the naming structure and try and blend in. As a precaution, the hacker begins to look for and identify accounts that have not been used for a long time. The hacker assumes that these accounts are likely either forgotten or not used so they change the password and elevate privileges to an administrator as a secondary account in order to maintain access to the network. The hacker may also send out emails to other users with an exploited file such as a PDF with a reverse shell in order to extend their possible access. No overt exploitation or attacks will occur at this time. If there is no evidence of detection, a waiting game is played letting the victim think that nothing was disturbed. With access to an IT account the hacker begins to make copies of all emails, appointments, contacts, instant messages, and files to be sorted through and used later.
read also = The Five phases of hacking process
read also = 5 step hacking process
- Clearing Tracks (so no one can reach them): Prior
to the attack, the attacker would change their MAC address and run the
attacking machine through at least one VPN to help cover their
identity. They will not deliver a direct attack or any scanning
technique that would be deemed “noisy”.
Once access is gained and privileges have been escalated, the hacker seek to cover their tracks. This includes clearing out Sent emails, clearing server logs, temp files, etc. The hacker will also look for indications of the email provider alerting the user or possible unauthorized logins under their account.
Comments
Post a Comment